Adaptive Yacht Cybersecurity Concept: Scalable Architecture, AI Technologies, and Independence Strategy
Executive Summary
We offer more than just a set of equipment; we provide a flexible methodology for building a cyber defense system adapted to the unique characteristics of each vessel. Our approach recognizes that a 40-meter charter yacht and a 120-meter expedition gigayacht have fundamentally different risk profiles, technological processes, and budgets.
The fundamental principles of Defense-in-Depth and Zero Trust remain unchanged, but their technical implementation is scalable. We analyze the actual onboard technological processes—from simple navigation systems to complex integrated bridges and Industrial Control Systems (ICS)—and build protection precisely around them.
The key elements of our strategy are ensuring the customer's technological independence and using advanced AI technologies to counter modern threats without the risk of interfering with critical vessel processes.
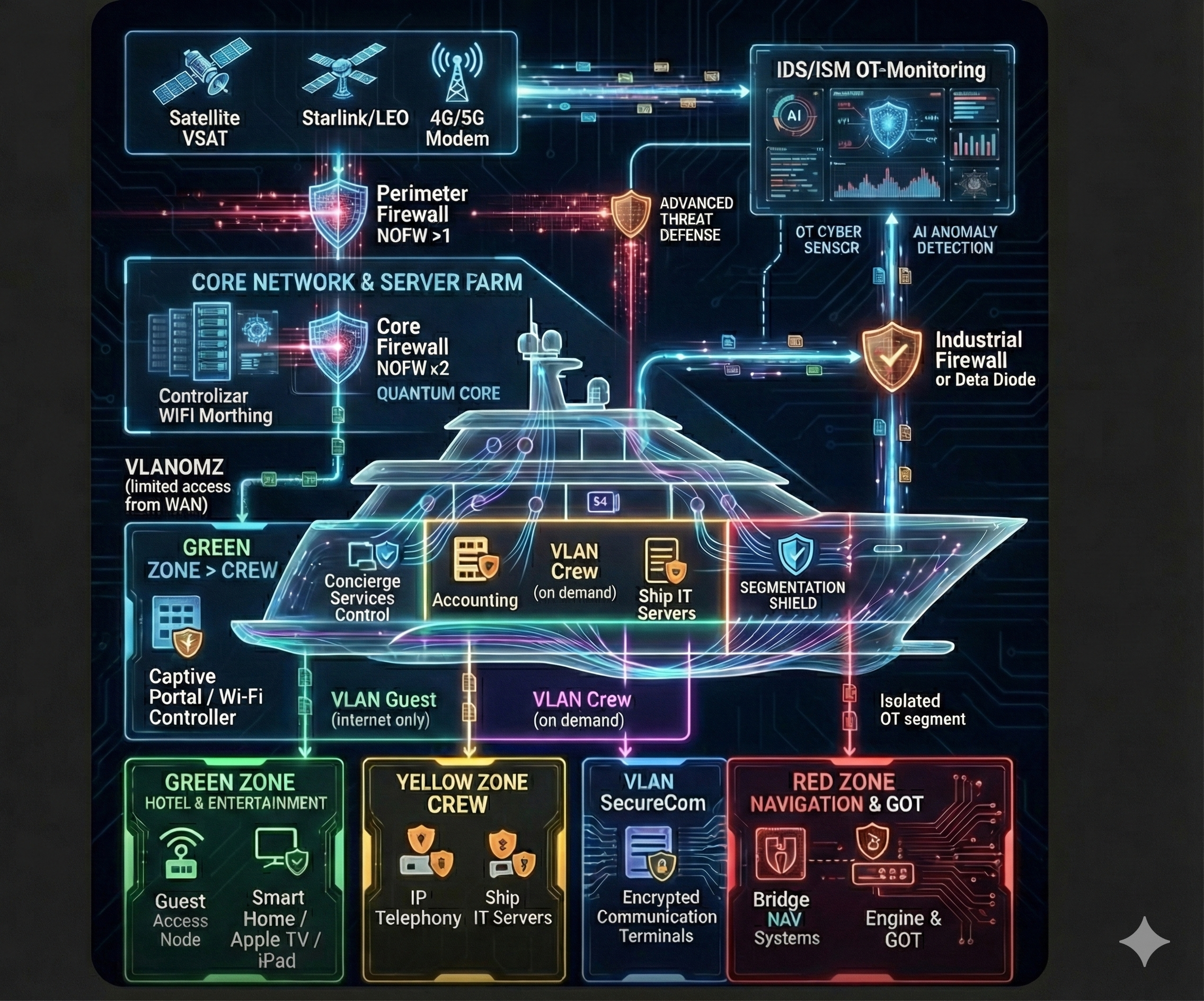
1. Scalability of Architecture by Yacht Class
We do not impose redundant solutions. The complexity of the architecture directly depends on the vessel's size, the saturation of its IT/OT systems, and its purpose.
Variant A: Compact Yachts (up to 40m) / Economical Profile
Focus: Basic perimeter protection, separation of guest and crew networks, protection of critical navigation equipment.
Implementation: Often uses converged equipment (e.g., a unified UTM - Unified Threat Management device) combining the functions of a perimeter gateway, internal firewall, and Wi-Fi controller.
Segmentation: Simplified (Guests / Crew / Navigation).
Variant B: Mid-sized and Large Yachts (40m - 80m) / Standard Profile
Focus: Full implementation of the Defense-in-Depth architecture. Dedicated devices for each function, deep segmentation, active monitoring.
Implementation: Separate clusters for the perimeter and network core. Dedicated WLAN controllers. Deployment of industrial gateways for the OT segment.
Segmentation: Detailed (Guests, Entertainment, Crew-Admin, Crew-Personal, SecureCom, OT-Navigation, OT-Engines).
Variant C: Gigayachts and Expedition Vessels (>80m) / High Profile
Focus: Maximum fault tolerance, redundancy of all critical nodes, protection of complex ICS, advanced AI-based threat detection systems.
Implementation: Geographically distributed onboard Data Centers, use of Data Diodes for physical isolation of critical segments, deployment of a local SIEM system and a 24/7 SOC (Security Operations Center).
2. Strategic Advantage: Artificial Intelligence as an Advisor
In the modern cyber threat landscape, the use of AI technologies has ceased to be an option and has become a vital necessity. Attackers increasingly use AI to automate attacks, search for vulnerabilities, and bypass traditional security measures. To withstand this, one must possess similar, or ideally superior, cyber weapons.
However, we understand the specifics of marine vessels, where navigation safety is paramount. Therefore, we implement ML and AI-based solutions with strict authority limitations:
Principle of Non-Interference:
Our AI systems operate exclusively in "passive observer" mode. They do not interfere with vessel management technological processes (OT/ICS) and technically cannot independently issue commands to actuators (engines, steering).
Deep Monitoring and Analysis (NTA/UEBA):
AI continuously analyzes massive volumes of network traffic and user behavior patterns in real-time. It is capable of revealing hidden, non-obvious anomalies indicating preparation for a complex attack that a human or signature-based antivirus would simply miss.
Intelligent Alerting and Recommendations:
The system filters out "information noise" (false positives) and instantly informs the crew or shore-based service only about real threats. The AI does not just signal a problem but provides ready-made action recommendations for its localization, significantly reducing reaction time in a critical situation.
3. Implementation Strategy and Vendor Policy
The choice of specific technical solutions depends on the customer's budget and risk management strategy. We offer three approaches to selecting the technology stack.
Approach 1: Enterprise (Branded Solutions)
- Description: Building the system based on products from leading world vendors (Palo Alto Networks, Fortinet, Cisco, etc.).
- Pros: Unified ecosystem, guaranteed support, advanced out-of-the-box AI functions, regulatory compliance.
- Cons: High Total Cost of Ownership (TCO), risk of vendor lock-in, potential sanctions risks.
Approach 2: Open Source (Solutions with Open Source Code)
- Description: Using proven, reliable Open Source products (pfSense/OPNSense, Suricata, Zeek). Modern Open Source solutions also actively integrate machine learning modules.
- Pros: No licensing fees, full code control, absence of hidden "backdoors", independence from manufacturer policy.
- Cons: Requires high expertise for implementation and maintenance (our team takes care of this).
Approach 3: Hybrid (Balanced Mix) — Recommended
- Description: Strategic combination of the best Enterprise solutions and reliable Open Source products across different defense echelons.
- Strategic Advantage (Cyber Defense Frontier): We view the absence of technological monoculture as an additional layer of security. If a critical vulnerability is discovered in a key vendor's product, it does not compromise the entire system, as other echelons are built on different technologies.
- Pros: Budget optimization, reduction of vendor dependence risks, flexibility in modernization.
Conclusion
Our goal is to create a cybersecurity system that does not just meet standards but realistically protects a specific vessel using the most modern yet safe technologies, including AI. By offering flexibility in architectural choice and vendor strategy, we guarantee that the solution will be cost-effective, technologically independent, and ready for any challenges of tomorrow.